Once a year, maybe twice if they’re cautious, businesses invite a third party to find holes in their defences, patch a few, file the PDF report, and move on. The assumption is that the security picture stays the same, but it doesn’t, not even close
The reality is brutal: cyber threats don’t operate on a schedule. Attackers aren’t bound by your audit cycle. They don’t care about your compliance deadline. They move fast, they automate everything, and they never stop scanning for that one mistake, that one unpatched server, that one misconfiguration introduced by your development team last night. In this game, annual testing is simply outdated, and dangerously so.
We’ve entered an era where a once-a-year security assessment is the digital equivalent of checking a smoke alarm after the house has already burned down. Your infrastructure is changing too fast. Cloud environments are spun up and torn down in days. Developers push code multiple times a week. Teams integrate new SaaS tools without consulting IT. Remote users, mobile devices, third-party contractors. They all expand your attack surface in real time. Every change is a potential gap. Every oversight is a potential breach.
And while you’re waiting for the next pen test to roll around, threat actors are already inside someone’s network. Maybe even yours.
Penetration testing has traditionally served as a snapshot, a freeze-frame of risk, accurate only for that moment in time. But in today’s climate, that snapshot begins to fade the second the tester walks out the door. Within weeks, sometimes days, your environment has shifted, and the assessment is obsolete. It’s not that testing itself is flawed; it’s that the way we’re applying it is stuck in the past.
We need to stop thinking of pen testing as an event and start treating it as a process – living, continuous, and adaptive.
This shift is not just about staying ahead of attackers. It’s about evolving beyond compliance theatre. ISO 27001, Cyber Essentials Plus, PCI DSS. They all require “regular testing,” but let’s be honest: for many, compliance has become the ceiling rather than the floor. Organisations aim for minimum effort, hoping a ticked box will buy them another year of safety. But when your name is splashed across the headlines after a breach, no one asks if you were compliant. They ask why you weren’t prepared.
Fortunately, we now have the tools to do better.
Automated penetration testing platforms have changed the game
Instead of a single, labour-intensive engagement, businesses can now run continuous assessments weekly, monthly, or after every major change. These platforms simulate real-world attack techniques, report in real-time, and integrate directly with your remediation workflow. They don’t sleep. They don’t take breaks. They test as often as you need them to.
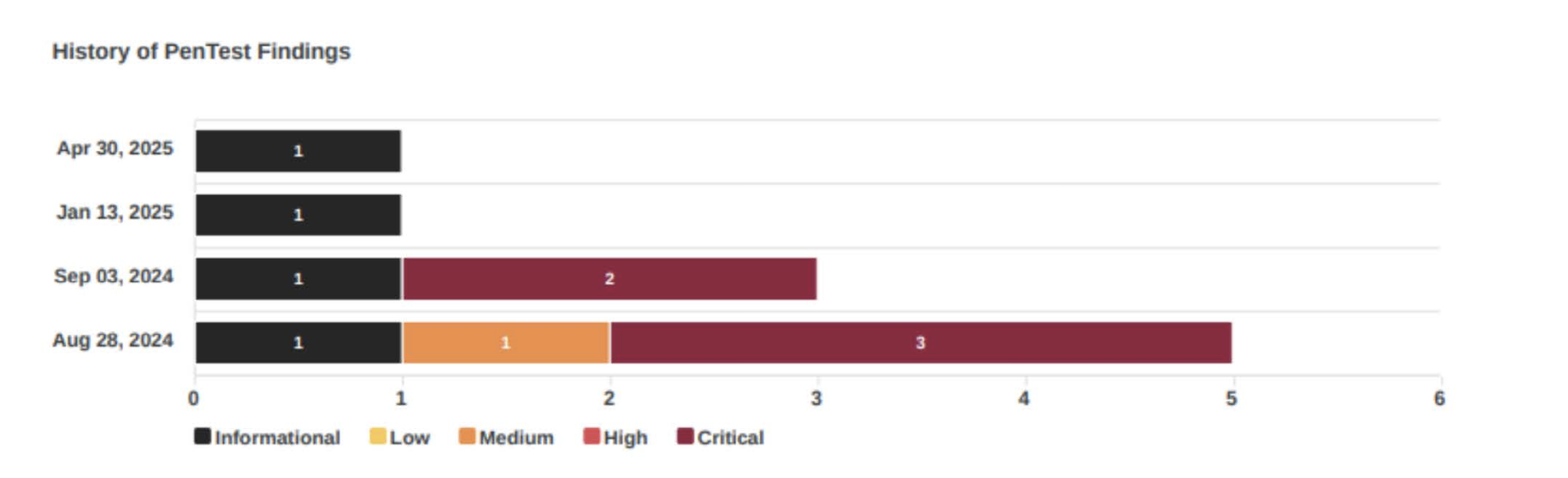
This isn’t an attempt to replace human expertise. Manual testing remains critical for deep, complex, and creative attack simulations. Automation fills the gaps between those engagements. It provides constant pressure, constant validation, and constant visibility. Think of it as a fire drill that never ends, one that sharpens your response, reinforces your controls, and gives your team the muscle memory to react under real pressure.
Continuous testing is now within reach for smaller businesses and mid-sized enterprises. Subscription models have replaced large one-off expenses. Setup is faster, integration is cleaner, and the results are more actionable. You don’t need a massive security budget to build a mature security posture; you just need the right approach.
This shift in mindset is about resilience. It’s about acknowledging that security isn’t a destination, but a journey that requires consistent course correction. You wouldn’t check your heart rate once a year and assume you’re healthy. Why do we treat our cyber health that way?
Continuous Penetration Testing as a Service
At Secure Nexus, we’ve built our services around this belief. Static security is insecure security. That’s why we deliver Continuous Penetration Testing as a Service and layering it with the real-world expertise of our experienced security engineers. We engage continuously, feeding intelligence back into your environment and helping your team close gaps before they’re exploited. We simulate the tactics of modern attackers. From privilege escalation and credential theft to lateral movement and data exfiltration, and we do it as often as your risk appetite demands. Our goal isn’t to scare you into buying more tools. Our goal is to help you build confidence – the kind that comes from knowing your defences have already been tested, refined, and tested again.
We tailor our testing frequency to your business. Monthly, quarterly, after major releases. Whatever cadence suits your operations. We integrate the results with your ticketing system, your SIEM, your dashboards. We don’t just show you the vulnerabilities. We help you fix them, measure progress, and track improvement over time, without breaking the bank.
Security isn’t a checkbox. It’s a mindset. In 2025, that mindset must be relentless.
The organisations that will survive and thrive in this threat landscape are the ones that stop treating security like a one-off audit and start treating it like a continuous commitment.
The ones that don’t ask, “Are we compliant?” but instead ask, “Are we resilient?”
Your next pen test should be more than a date on a calendar. It should be the beginning of a loop – test, learn, improve, repeat.
At Secure Nexus, we’re here to close that loop with you. Why not contact us about your next penetration test?
Defence in depth: Building layers of security in a modern threat landscape
Raymond Setchfield discusses building layers of security in a modern threat landscape within this defence-in-depth focus
A single security measure is no longer enough to protect an organisation from cyber threats. Attackers are persistent, sophisticated, and constantly evolving their methods. Defence in depth (DiD), a long-standing security principle, offers a comprehensive approach by implementing multiple layers of defence across an organisation’s systems, processes, and people.
This layered strategy aims to ensure that if one control fails, others remain in place to prevent or minimise the impact of a breach. It is not about relying on any single solution but about creating a security architecture where weaknesses in one area are compensated for by strengths in another.
The principle behind defence in depth
The concept originates from military strategy, where multiple defensive positions are used to slow down, detect, and repel attackers. In cybersecurity, the same principle applies: an adversary must overcome several layers before reaching valuable assets.
These layers are typically designed to:
- Deter: Make an attack more difficult or unattractive.
- Detect: Identify malicious activity as early as possible.
- Delay: Slow down an attacker’s progress, giving time to respond.
- Respond: Contain and mitigate the impact of an incident.
The layers of defence in depth
While the specific layers vary by organisation, most models include a combination of the following:
- Physical security
- Physical access to systems remains an often- overlooked security risk. Measures such as secure entry points, CCTV, server room locks, and visitor management systems prevent unauthorised individuals from physically tampering with equipment or gaining access to sensitive areas.
- Network security
- The network is a primary target for attackers. Segmentation, firewalls, intrusion detection and prevention systems (IDPS), and secure configurations can limit an attacker’s ability to move laterally if they gain a foothold. Network monitoring tools provide visibility into unusual traffic patterns that could signal an intrusion.
- Endpoint security
- Laptops, desktops, and mobile devices are common entry points for attackers. Security measures such as anti-malware, device encryption, application whitelisting, and endpoint detection and response (EDR) tools help secure endpoints against both external and insider threats.
- Application security
- Applications can be exploited through vulnerabilities if not properly secured. Secure development practices, regular patching, code reviews, and application firewalls help protect software from exploitation. The principle of least privilege should be applied to application accounts to limit the damage if they are compromised.
- Data security
- Protecting the data itself is essential. Encryption at rest and in transit, access controls, and data loss prevention (DLP) solutions ensure that sensitive information remains protected even if an attacker breaches other defences. Data classification schemes help identify what needs the highest level of protection.
- Identity and Access Management (IAM)
- Compromised credentials are a leading cause of breaches. Strong authentication methods such as multi-factor authentication (MFA), regular access reviews, and just-in-time access provisioning reduce the risk of unauthorised access.
- User awareness and training
- Even the most advanced technical controls can fail if users are unaware of threats. Phishing simulations, regular security briefings, and clear reporting procedures empower staff to act as part of the defence strategy rather than as potential weak links.
- Monitoring and incident response
- Effective logging, continuous monitoring, and well-tested incident response plans enable rapid detection and containment of threats. The faster a threat is identified; the less opportunity it has to cause significant harm.
The benefits of a layered approach
DiD provides several key benefits:
- Resilience:
- Multiple layers reduce the likelihood of a single point of failure leading to a catastrophic breach.
- Early detection:
- Monitoring across layers improves the chance of spotting suspicious activity before it escalates.
- Adaptability:
- Layers can be updated or replaced independently as threats evolve.
- Regulatory compliance:
- Many industry regulations require multi-layered security controls.
Common pitfalls to avoid
Implementing DiD comes with challenges. Over-reliance on technology is a common issue; tools are vital, but human awareness and sound policies are equally important. Poor integration between layers can cause inefficiencies or gaps, while neglecting maintenance leaves defences outdated and vulnerable. Flat network designs are another risk, as a lack of segmentation allows attackers to move quickly once inside.
Building an effective defence in depth strategy
It all begins with assessing the threat landscape to understand the risks specific to your industry, size, and operating environment. From there, it is essential to prioritise the protection of critical assets, focusing first on systems and data whose compromise would cause the greatest harm.
Layered controls should then be implemented, combining preventative, detective, and responsive measures across physical, technical, and administrative areas. Regular testing through penetration exercises, red teaming, and security audits ensures these measures remain effective. Finally, the strategy must adapt continually, as threats, business processes, and technologies evolve.
Defence in depth in the modern context
Modern threats such as ransomware, supply chain attacks, and cloud-based breaches highlight the importance of this approach. For example, if ransomware bypasses email filtering, it might still be stopped by endpoint protection. If that fails, network segmentation and backups can limit the damage and enable recovery.
In cloud and hybrid environments, DiD extends beyond the corporate network. Organisations must consider identity protection, API security, secure cloud configurations, and visibility across multi-cloud infrastructures.
The principle is also vital in supply chain risk management. A trusted supplier’s breach can be as damaging as a direct attack, so layered controls should extend to vetting and monitoring third-party access.
By embracing a multi-layered defence strategy, organisations position themselves not only to withstand attacks but also to detect and respond to them more effectively, ensuring business continuity and maintaining trust with customers and partners.


