The Horizon 2020 project SOCCRATES brings together some of the best expertise in the field to develop, implement and evaluate an automated security platform to defend against complex cyber-attacks, more of which is explained here by Reinder Wolthuis from TNO
Over the past few years, the cyber threat landscape has greatly evolved. Complex cyber-attacks are now conducted by professional threat actors that have substantial resources and (technical) capabilities. Such attacks are often targeted in nature and may involve a great degree of automation, persistence and (technical) sophistication. Meanwhile, the dependency on Information and Communication Technology (ICT) and, thus, the potential impact of any cyber-attack is ever increasing. Combined with the continuously evolving ICT infrastructures with diverse and emerging technologies, for example, the Internet of things (IoT), organisations are faced with a challenging task.
To deal with these challenges, many organisations have increased their efforts in security monitoring and incident response. Many have set up internal Security Operation Centres (SOCs) and Computer Security Incident Response Teams (CSIRTs) to perform these tasks, others outsourced these tasks to a Managed Security Service Provider (MSSP). In recent years, these security operation activities have been extended to the collection and processing of Cyber Threat Intelligence (CTI), to anticipate upcoming threats and take appropriate precautions. Although these security operations have received more attention over the years, these SOCs and CSIRTs (both internal and MSSP) are now faced with challenges:
Improve and extend detection capability
Threat agents (attackers) continuously evolve and improve their Tactics, Techniques and Procedures (TTPs), including stealth techniques. The SOCs also need to improve the detection capability with more advanced techniques that assist the analyst in discovering indicators in a massive amount of data or reducing the number of false positives.
Automate the CTI process
As the amount of available CTI is increasing and the value of a large portion of that CTI is limited to a short time span, it is becoming more important to automatically assess and apply mitigation strategies to these threats.
Understand the ICT infrastructure
Simply put; you cannot defend what you don’t know. As SOC analysts need to interpret and understand the detected security events, insight in the continuously evolving ICT networks and systems is essential. The SOC analyst also needs to understand the critical attack surfaces, attack vectors that may lead to a compromise of critical business assets as well as defence mechanisms deployed to counter attacks.
Assess the business impact of an incident
In addition to understanding ICT infrastructure, the SOC analyst needs to be able to assess the potential impact on the business of an ongoing attack or emerging threat. Business processes, thus, need to be mapped on the ICT infrastructure components, and insight into the consequences of a breach of confidentiality, integrity and/or availability of system resources or information assets needs to be (near real-time) available.
Recommend Course of Actions (CoAs)
When faced with an attack or emerging threat, the SOC analyst needs to identify possible responses and determine which response is the best given the ICT infrastructure, available (on demand) reconfigurable security functions, and the effect on the business.
Attribute attacks to known adversaries
When engaged in an ongoing attack, it is beneficial to attribute the attack to a known adversary. This will improve forensics capability and ability to predict next steps.
SOCCRATES (SOC & CSIRT Response to Attacks & Threats based on attack defence graphs Evaluation Systems) is a Horizon 2020 project, led by TNO, that supports the SOC and CSIRT community in overcoming these challenges. The SOCCRATES partners are depicted in figure 2. The main project objective is to: ‘Develop and implement a Security Decision Support framework that enhances the effectiveness of SOC and CSIRT operations.’
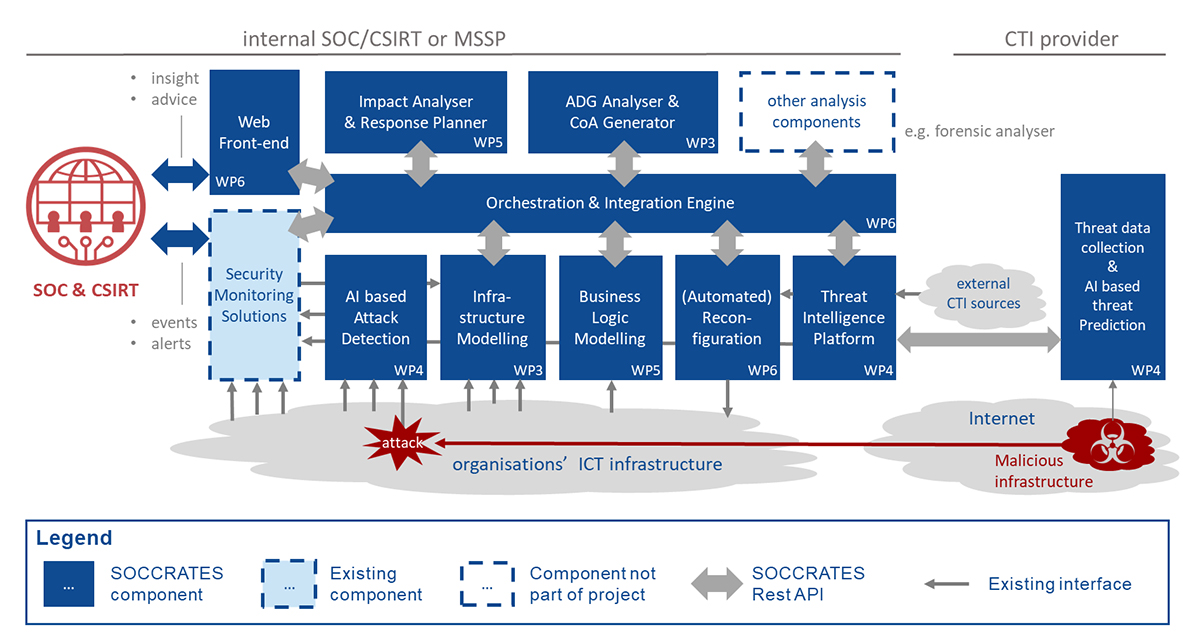
The integrated Security Decision Support framework will consist of a platform with a modular set of components with standardised interfaces and a central orchestration function, see figure 1.
The platform is a mix of technical innovations, which aim to increase the insight in the propagation of threats and cyber-attacks within the organisation’s ICT infrastructure, increase the insight in the business impact, increase the attribution to known adversaries, and increase the capability to effectively respond in an informed manner.
The platform will be built in three iterations between 2019 and 2022 and will be evaluated in three pilots organised by Mnemonic (Managed Security Service Provider), Vattenfall (internal ICT SOC) and Shadowserver (CTI collection, processing & analysis).
We would like to invite interested parties to join our stakeholder group to get actively informed on the project deliverables and interact with the project members. See the contact details below.
SOCCRATES has received funding from the European Union’s Horizon 2020 Research and Innovation program under Grant Agreement No. 833481.