Risk management and information governance are two core governance activities. Without both disciplines in place, few organisations can expect to achieve sustainable success. While they are essential separately, they complement each other
In this e-book, we will explore how information governance is core to effective risk management.
Defining Information Governance
Information governance is about how we look after the information we hold and make the best possible use of it.
Information includes all the data and records held by an organisation. Information is defined best as the collation of data and records for use in specific contexts.
This includes corporate information as well as personal data – anything that by itself or in combination with other information generates value by allowing decisions to be made, products to be developed/sold, or ensures compliance with statutory duties.
Governance is the system of direction or control that ensures a system performs well and delivers its strategy. It provides the framework of accountability and oversight to provide assurance that activity is well managed.
Information governance can therefore be defined as “the system of direction or control that enables the data we hold to have meaning and allows decisions to be made”.
For most organisations, this is primarily achieved by developing an information governance framework.
Information is an asset
Because information delivers value, it is an asset that can and should be used to deliver your objectives. It must also be used safely and securely, and you need a system of control to manage the information you hold.
Within your information, governance framework you will assign responsibilities, and decision rights, and specify security arrangements, training requirements and reporting/oversight lines.
In many ways, effective information governance can be like effective financial management. Income and expenditure are carefully managed to keep organisations viable and ensure they meet their goals. Information is an asset and has value, much like money.
When it comes to money, organisations must know:
- How much they have
- What they are using it for
- That it is safe and secure
- Who has access to it, and how much.
The same is true for information
It is important to have timely, accurate and high-quality information to inform decisions and measure performance. The higher the quality of the information the greater its value as an asset.
Risk management information governance is proactive, so it does not just work to manage the information that you have. It also looks forward to information that you may need in the future, and how you may use the information that you currently have in new ways.
The best information governance systems plan for:
- What information is needed;
- Who will have access to it;
- Build in privacy and security as part of the design process;
- Think about the point at which the information is destroyed;
- Assign responsibility for delivery
When it comes to risk management it is clear that effective information governance will be crucial to defining risks, informing risk approaches, and providing assurance that risk management is effective.
Defining Risk
Taking risks is part of what any organisation does to achieve its objectives. However, organisations must also be careful about the amount of risk they take on. Too little, and their competitors will outperform them. Too much, and they may fail.
Risk management is about identifying and managing potential problems (and opportunities) to make achieving objectives more likely.
The key thing about risk management is that it is proactive – looking forward to trying and identifying possible problems.
Risk management can be seen being applied in all sorts of settings notably business continuity; finance; health and safety; security; contracting etc. However, risk impacts all areas of work and is not something that can – or should – be avoided.
Effective risk management means
- Fewer shocks and surprises;
- Better targeting of resources;
- Avoiding distractions and reacting to crises;
Risk management is key to good governance. It is also crucial that risk management is based on accurate and up-to-date information. Hence the link between risk management and information governance.
One of the most important things to understand is that risk is an uncertain event. Something that could happen, not something that has happened. Something that has happened is known as an issue and sometimes you might see a ‘risk and issues’ log attached to a project or programme. Because a risk is something that could happen, risk management is about looking forward and, put simply, avoiding problems before they happen – or avoiding the worst outcomes if they do happen.
A culture that does not appreciate risk management, or devote resources to it, is less likely to succeed.
Because risks are things that could happen, they are made up of two parts: likelihood (chance of the risk happening) and consequence (the impact of the risk happening). Typically, likelihood and consequence have a value attached to them, and those values are multiplied to give an overall risk score. The higher the score, the greater the risk.
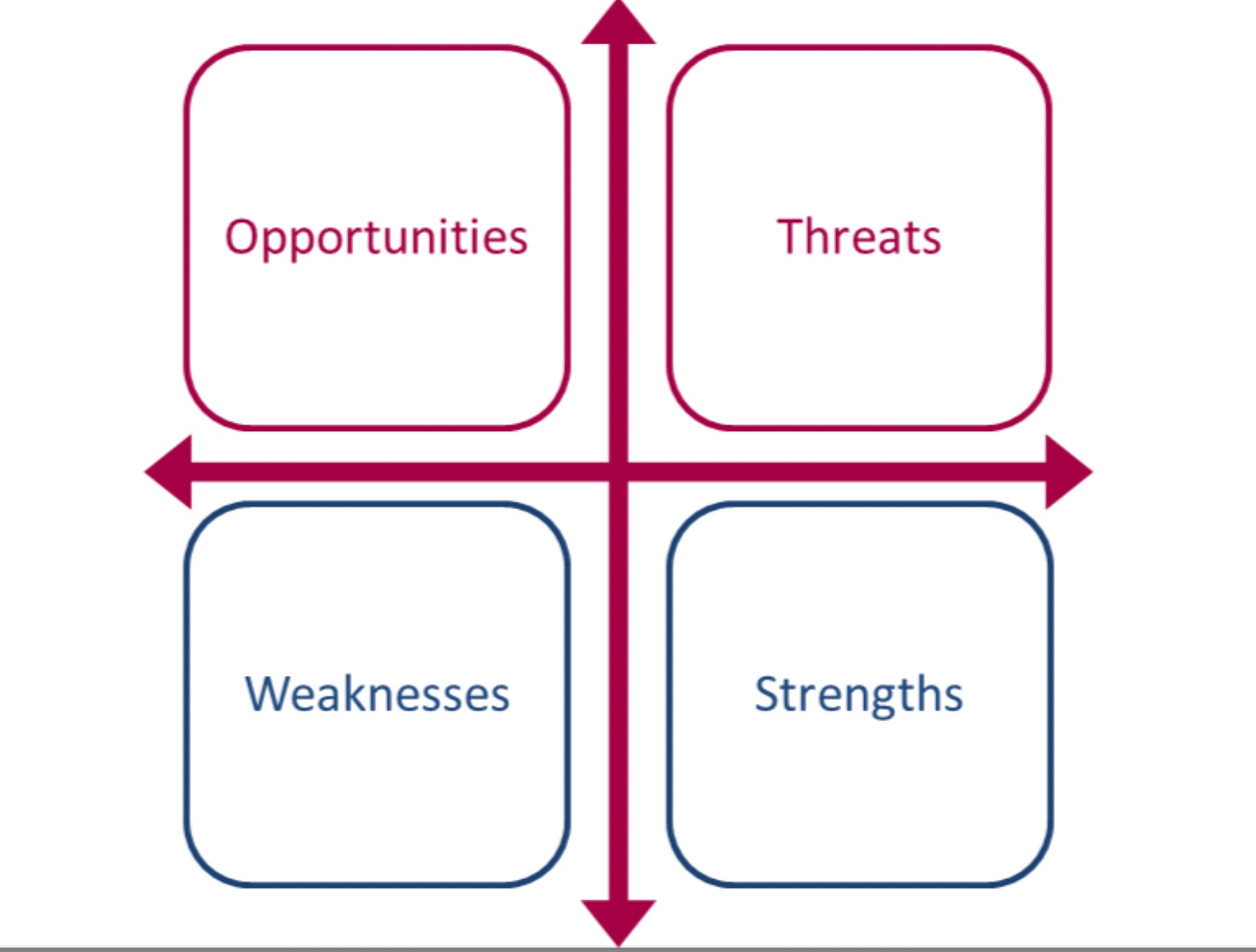
Identifying Risk
A great way of identifying risks is to do a SWOT analysis. SWOT stands for Strengths, Weaknesses, Opportunities and Threats.
Risks are opportunities and threats, as these are uncertain – things that may occur. Strengths and weaknesses are certain – things that have happened (the issues). You manage these reactively and as such, they don’t fall within the scope of risk management.
Another tool you can use is a PESTLE analysis. PESTLE stands for:
- Political
- Economic
- Social
- Technological
- Legal
- Environmental
Using a PESTLE analysis, think about the opportunities and threats that face your organisation in each of the contexts listed above.
Once you have identified your risks you must score them by assessing their likelihood and consequence. This will give you your initial risk profile, and help you decide how you will manage your risks going forward.
How Does Good Information Governance Help Identify and Manage Risks?
Effective information governance will clearly help you identify and evaluate risks, whatever method you use to identify them. The better and more reliable the information you have the better your risks will be defined. Effective information governance will also help you manage your risks on an ongoing basis.
The more reliable and high-quality the content of your information assets the better your risk management will be because:
- You will be able to identify your risks more effectively
- You will be able to evaluate likelihood and consequence more accurately
- The actions you will take to manage your risks will be better informed.
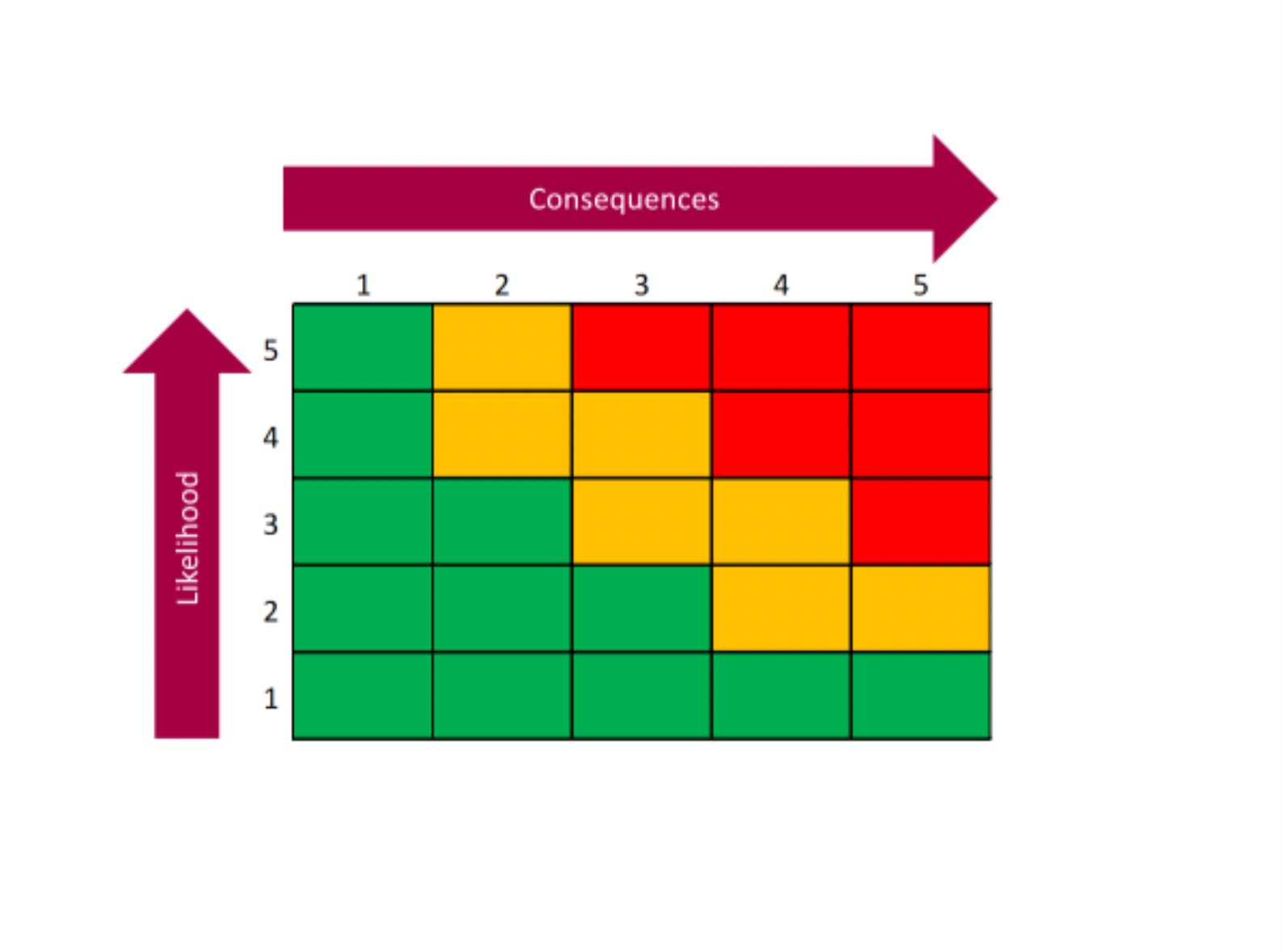
Evaluating Risk and Defining Your Risk Approach
You must have a way of scoring risks, and this means you need the information to evaluate the likelihood and consequence of risk. There are different ways of scoring risks but one of them is to use a five-by-five matrix where likelihood and consequence go on a scale of one to five, which five being the most likely or greatest consequence. Multiplying the two together gives you a range of risk scores, going from one to 25.
The higher the risk score the greater the attention you are likely you want to pay to it – and it is important to be sure you are using the information you must determine the right likelihood and consequence for any given risk. Otherwise, your risk approach may be the wrong one, and you may not be prepared if the risk becomes an issue.
Once you have made a well-informed attempt to score your risk you need to identify your risk approach – that is, what are you going to do about the risk, if anything?
There are four main risk approaches:
- Accept: do nothing. This typically applies to lower-rated risks or risks that pose no material threat.
- Mitigate: this is where you take action to reduce the likelihood or consequence, or both. Most risks will have some form of mitigation action.
- Share: some larger risks need to be shared to be managed. A straightforward example of this is taking out insurance to help mitigate the risk of a loss.
- Avoid: the very largest risks may be greater than you are willing to bear. This means you will want to avoid the activity that poses the risk in the first place.
Having the right information assets available will help you both score risks and by extension decide on the most appropriate risk approach.

Case Study 1: Building a Bridge
Imagine a contractor building a road bridge over a river. Once completed, the bridge will be handed over to a local authority for management and maintenance. The specification for the bridge calls for a working life of over 100 years.
There are some key questions to answer here.
- Where are the risks, and who is affected by them?
- What information would be needed to manage the risks?
- How can we be sure the right people get the right information at the right time?
The contractor will want to build the bridge on time and on budget and ensure it is of sufficient resilience to meet the design specification.
The local authority will need the information to run and maintain the bridge.
When building the bridge the contractor will experience a number of risks:
- Geological
- Quality of components
- Health and Safety
- Labour availability
- Bad weather hampering construction
- Fraud
- The end client’s local authority may not take on the bridge when it is complete
The local authority will also face risks
- Component failure during the working life of the bridge
- Land subsidence or the river flooding
- The bridge getting more heavier traffic than designed for
- A lack of construction information increases maintenance time and cost
All these risks can be mitigated with effective information. For example, the contractor building the bridge will undertake geological surveys before construction begins.
Effective information governance will ensure those geological surveys are retained because they will:
- Help reassure the client’s local authority that the bridge was well constructed, helping them take it on once complete and;
- The local authority can use the information to mitigate the risks of future land subsidence and plan accordingly.
Similarly, to mitigate risks for the client’s local authority the contractor will need to obtain and retain detailed records of the source and quantity of components used in the bridge.
This will help both parties in several ways:
- The contractor will be able to manage costs and help assure the local authority that the bridge was built appropriately.
- The local authority will have confidence in taking on the completed bridge because appropriate information will show there is a low risk of doing so.
- Also, if a maintenance issue occurred the risk of excessive costs or time performing maintenance or repairs is reduced as the local authority knows what components were used in the bridge, how, and from where they were sourced.
These examples are just some of the ways in which effective information governance supports effective risk management and reduces risk overall.
Defining Risk Appetite and Tolerance
An important part of effective risk management is defining the level of risk you want to take as well as the maximum amount of risk you are willing to tolerate.
The amount of risk you want to take is your risk appetite, and the maximum amount of risk you are willing to tolerate is your risk tolerance.
Having a healthy risk appetite will stop you from being too risk averse, and your risk tolerance will tell you when you should escalate risks to ensure they receive the right attention and actions are taken to reduce them.
This is a difficult one to get right – too risk-averse and you could have a huge risk profile, leading to paralysis. Conversely, failing to escalate risks to the right level is a quick way to ensure organisations lose sight of what is really happening.
Risk appetite and tolerance will vary by context. A new tech start-up might be very tolerant of financial risk for example but not necessarily of operational/technical or reputation risk.
Similarly, your tolerance for health and safety or safeguarding risks might reasonably be very low and could be escalated for further action even if overall risk scores are very low.
Knowing where risks sit in terms of your organisational attitude to risk will help tell you how much information you need to manage risks, how much you need to check risks are being managed well, and the point at which you will escalate risks for action and assurance.
These are examples of industries that use high-quality information to effectively manage risk:


Case Study 2: Equifax
Sometimes a failure to manage risk and to have the appropriate information governance systems in place to reduce risk can have real-world consequences.
An example of this is the data breach that occurred at Equifax in March 2017. The breach involved the data of 143 million people in America, Britain and other countries being stolen. However, there are a number of other features that emerged after the incident was first made public that suggest poor information governance and risk management contributed to the incident.
Although very large, it wasn’t the largest data breach ever. There were two others in 2017 alone that included data about over a billion people. It is however by far one of the most serious.
Equifax lost highly personal data including social security numbers. These are often used in America to provide identity and therefore expose the victims to a high risk of identity fraud. Victims’ data could be pooled with other stolen information to facilitate other types of fraud such as tax evasion.
From the perspective of good information governance and risk management, there is a range of issues to consider.
First and foremost, it is important to consider: the hackers who caused the breach were able to get into Equifax’s systems through a known vulnerability. A ‘patch’ for this breach was available but had not been systemically applied. Poorly planned and executed information security suggests fundamental flaws in information governance. The sensitivity of the data stolen is of particular concern, as the organisation should have treated it as riskier than it did.
The second issue is the delay in disclosing the breach. The attack that caused the breach occurred between May and July 2017. However, Equifax took about six weeks to make it public. Such a delay is indefensible for a company that relies on trust in its relationships with both businesses and individuals. Equifax’s share price fell on news of the breach, from $142 to just under $93. This fall wiped more than $6.75 billion off the company’s value.
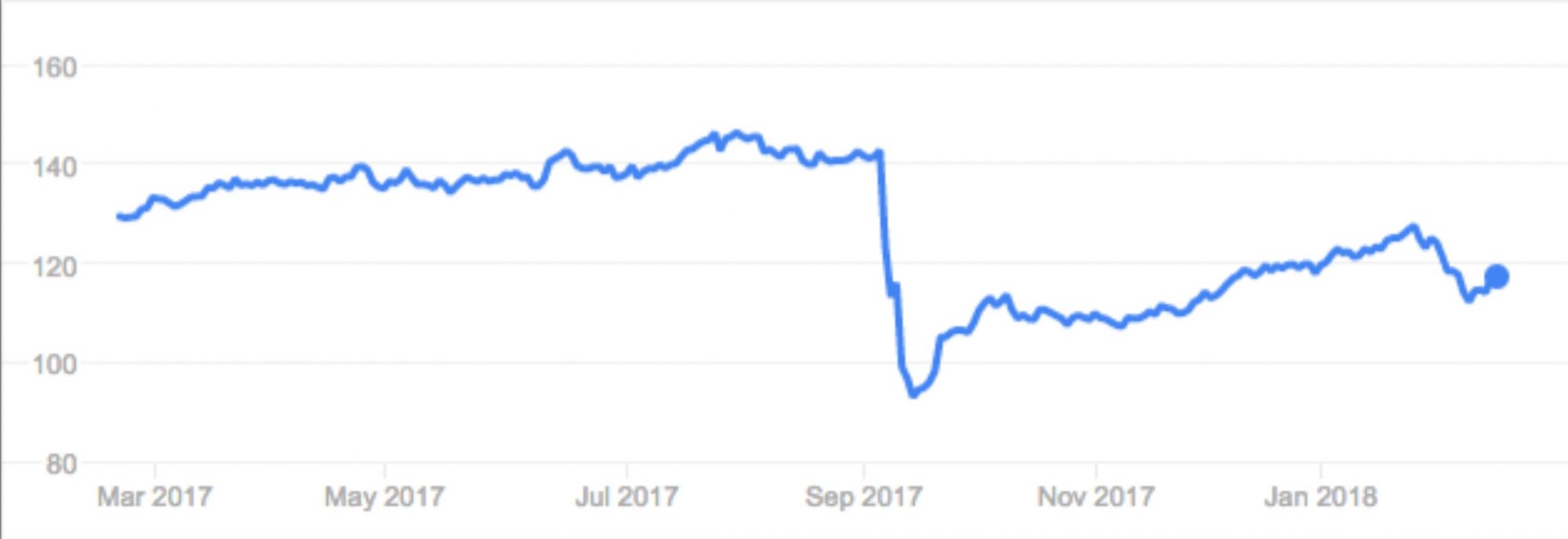
There is also the way it was handled. The company accidentally but repeatedly referred people who may have been affected by the breach to a fake phishing website potentially exacerbating the problem. In fact, perhaps ironically, the phishing site was set up to prove how potentially easy it is to dupe people into handing over their information. It had a banner that read “Cybersecurity Incident & Important Consumer Information, Which Is Totally Fake, Why Did Equifax Use A Domain That’s So Easily Impersonated By Phishing Sites?”.
Equifax’s real website was criticised for appearing to link support for victims with a promise not to take legal action in relation to the breach, although the company did clarify that this was not the case. In addition, many have wondered why the website Equifax set up to help people check if they had been affected by the breach had a bespoke domain, making it harder for people to be sure whether it was real.
There are clearly several significant questions about how the response was handled and whether there was an effective management plan in place to handle a data breach of this type. Equifax’s risk management processes and assurances to the Board on the adequacy of IT security were outdated, based on bad information, or in practice poorly scrutinised. Given the failure to manage a known vulnerability in their systems, this is particularly problematic as the foundation of Equifax’s business is the processing of people’s personal and financial information for credit checks and similar activity. Information security and the risks of a data breach – operational, financial, and reputational – should have had a much greater priority and much greater oversight.
Best practice – enabling Board leadership, being open with the public, and rapidly putting in place a carefully developed plan to recover from the incident – would not have mitigated the loss of the data (although effective risk management might have prevented it). It would have gone a long way to saving Equifax’s reputation and company value. It might have prevented the government scrutiny, and the civil and possible criminal cases coming Equifax’s way.
All organisations must implement robust information governance and risk management systems and check and challenge those systems at both operational and Board levels so that everyone is sure they understand the risks and can trust that appropriate action is being taken to manage them.
Part of doing this will be dependent on understanding your appetite for and tolerance of risk for all the different activities your organisation undertakes.
Risk Assurance and Risk Maturity
The next way in which effective information governance supports risk management is assurance. Risk assurance is simply evidence that your risk approach is both appropriate and effective. You need high-quality information to show that risk management is working well. For example:
- People who oversee/authorise your project need to be assured that you are managing your risks well.
- Auditors/the Audit Committee/trustees (whichever applies to your organisation) need to be assured that corporate-level risk management is working.
Because risk assurance is entirely evidence-based you must be able to provide high-quality information and manage it effectively to support this crucial element of risk management.
Finally, all risk management activities can be assessed for their maturity. Risk management is an ongoing cycle, and the collation and analysis of information to define, evaluate and manage risks should be continuous. To be effective risk management must be:
- Visible
- Consistent
- Repeatable
- Forward looking
- Ongoing
For the most mature risk systems, information assets are interrogated on a regular basis to ensure an organisation’s risk management adapts to changing circumstances.
Find Out More
To find out more about risk management, information governance, or a range of other governance activities visit our website. There you will find a range of free resources and events, and details of expert-led training courses available in a range of settings.
Read and Download the full eBook ‘Risk Management and Information Governance’ here


